- Firepower Configure Manager Delete
- Firepower Configure Manager Addon
- Firepower Configure Manager Add Dontresolve
Firepower Configure Manager Delete
Add a manager (Firepower Management Center) configure manager add IP address or hostname The registration key is a unique key that you need to enter on both the firewall and FMC. This can be anything at all that you make up but must match on both sides. The management interface had a configuration but had no gateway assigned to it. This was confirmed with the “show network” command. In my case for this test setup, my FMC and management vlans are not the same, so I needed that gateway for things to work. I tried reconfiguring the management port once more manually with the process.
*UPDATE** – See comments and now my own experience. This method is NOT working on FPR-1010 devices (and possibly 2000 and 4000 series as well). This was tested with 5506, 5508, and 5516 devices. I will be creating a new process and posting separately.
This guide is something that I have seen requests for in multiple places including the Cisco supportforums. I recently had to complete this process for some new Cisco Firepower FTD firewalls so I am going to document it. Without further ado, how to add a remote Firepower firewall to a local Firepower Management Center.
Look above to see a sample diagram of what we are looking at as our end goal. After the guide below, that is what our topology will look like.
I have an enterprise main campus and smaller remote sites, such as the one we are working with today. This site has a Firepower 5506X running the FTD image. I want to manage this firewall (and the others) with Firepower Management Center (FMC). Normally the process would be easy if this firewall was onsite at my main campus. I would just follow this easy guide Cisco provides. This case is different though. My remote site has a single static IP. I don’t have a second public, routable IP address that I can assign the management port so I can register the firewall with FMC. That is the reason for this guide. It’s not too crazy, but there are some important details to follow. This process we will be using today was partially outlined in a published Cisco Doc, but a few steps were still unclear. I am working from that doc and adding in the rest of the details I was looking for in more of a step by step guide. Let’s get started.
Configuring the Remote Firepower Firewall and FMC
Port-Forwarding – Main Campus
Very quick note on step one. You need to setup port forwarding on your main campus firewall for port TCP8305. The end goal is that the FMC will send and received the TCP8305 traffic as your outside, public IP address for each of these remote Firepower firewalls. Your main campus will also need to allow the TCP8305 traffic in both directions in its ACLs.
Lotus exige gt4. Lotus Evora GT4 The Lotus Evora GT4 is designed to provide a competitive racing package straight ‘out of the box’. Its lightweight chassis and the composite and carbon fibre body provide a surprising amount of cockpit space, despite the compact exterior dimensions. Category Porsche Cayman GT4 Lotus Exige S (V6) Track Performance: 669: 664: Straight line speed: 1392: 1609: Total: 2061: 2273. The first step in a return to international racing for one of the most famous names in motorsport, Lotus have announced a brand new Evora GT4 Concept. Using over 70 years of engineering innovation on road and track, the iconic company has unveiled its latest, British-built. The Lotus Exige 410 & The Porsche 718 GT4 For years, Lotus have embodied this philosophy of producing a mad mini attainable supercar. The Elise is one of the smallest sports cars in the world, and the Evora is one of the cheapest supercars you can buy.
Initial Management Port Setup
Assign management port an IP address (the one that will eventually be the outside interface)
- configure network ipv4 manual 10.0.0.X 255.255.255.0 10.0.0.1
- **Note** – change this info out with your public IP address for the remote location.
Add a manager (Firepower Management Center)
- configure manager add < IP address or hostname > <registration key>
- The registration key is a unique key that you need to enter on both the firewall and FMC. This can be anything at all that you make up but must match on both sides.
- If your FMC and FTD Device are separated by a NAT device like another firewall or NAT’ing router, you need to use a different command:
- configure manager add DONTRESOLVE <registration key> <id>
- The key is the same function as the other command but then you select a random number as a “unique NAT ID”. You will need to enter this on the FMC as well.
- Reference: https://www.cisco.com/c/en/us/support/docs/security/firesight-management-center/118596-configure-firesight-00.html
- The key is the same function as the other command but then you select a random number as a “unique NAT ID”. You will need to enter this on the FMC as well.
- configure manager add DONTRESOLVE <registration key> <id>
Firepower Configure Manager Addon
Connect the firewall to FMC
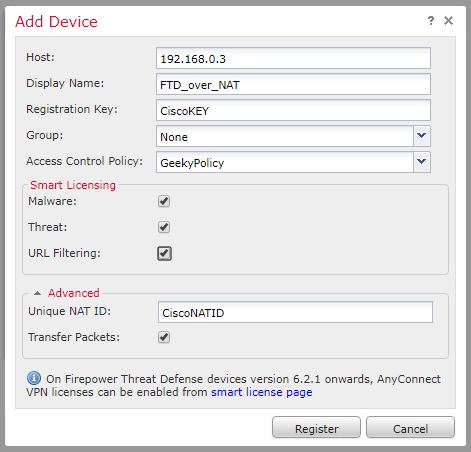
- Log into your FMC and add the device. You will need the public IP you assigned in step 1 and the registration key.
- Then, go to Devices -> Device Management -> and click the Add Device button in the top right corner from within FMC.
Access Policy Creation
- Once the device is added, create the following access policy. This trusts the traffic on port TCP8305 that FMC uses in both directions. Sub in your IP addresses for the ones below. This would be your public, outside subnet IP address and then the internal IP that you will eventually assign to your management port.https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/200868-configuring-firepower-threat-defense-ft.html#anc12
NAT Policy Creation
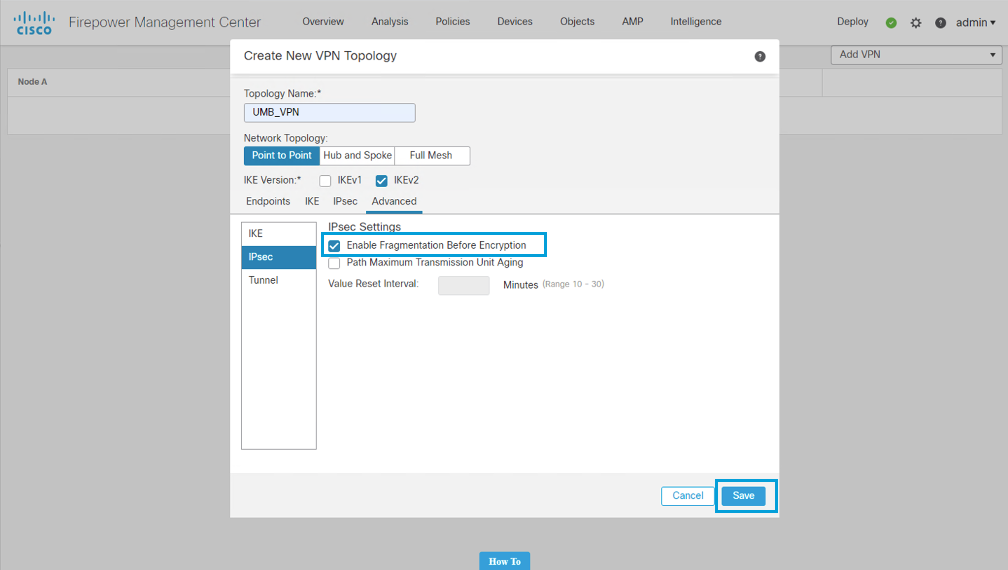
Create the NAT policy below. This NAT policy translates the internal management IP to the outside, public IP address for port TCP8305. There are two rules, one for both source 8305 and destination 8305 traffic as sometimes the FMC initializes the traffic and sometimes the firewall itself will.https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/200868-configuring-firepower-threat-defense-ft.html#anc12
Firepower Configure Manager Add Dontresolve
Configure new interface settings
Configure your inside and outside interfaces. Your outside interface will be the same IP address that your originally assigned to the firewall management port in step 1. Your inside IP address needs to be on the same subnet as the internal management IP you selected earlier.
Deploy all changed settings
Now that all your settings are entered and the policies are all created, you can deploy the settings. This is enough to connect the firewall to Firepower Management Center fully and allow the firewall to work as we need it to in the remote location.
Rearrange the Cables

Pixel gun 3d pocket edition hack apk. Now you need to move the cables around. Connect the interface designated as the inside to your switch at the remote location. Connect a cable from the management port to this same switch. Lastly, connect the internet circuit to the interface you designated as the outside interface.
Change the management port
- Console into the firewall and change the management port IP address one more time. Remember that internal subnet management IP you used earlier? You want to use that here. In the case of the images above, that would be 192.168.0.100. Same command that was used earlier:
- configure network ipv4 manual 192.168.0.100 255.255.255.0 192.168.0.1
Verify
Now, because you created the NAT rules earlier concerning port 8305, Firepower Management Center should be able to communicate with your firewall. Any traffic to the outside interface on TCP8305 will be port forwarded to the management port. You can now use your local Firepower Management Center to manage a remote Firepower firewall. You can add more access policy rules, configure more NAT rules such as a dynamic NAT rule, etc. FMC should have what it needs to finish the configuration.
[…] off, this post is a response and an update to my previous post on the subject, found here: Add Remote Firepower Firewall to Firepower Management Center. This process that we are talking about is about adding a remote Firepower firewall to a Firepower […]
